Aqua Container Security Api

Aqua security surfaces attacks on container platforms.
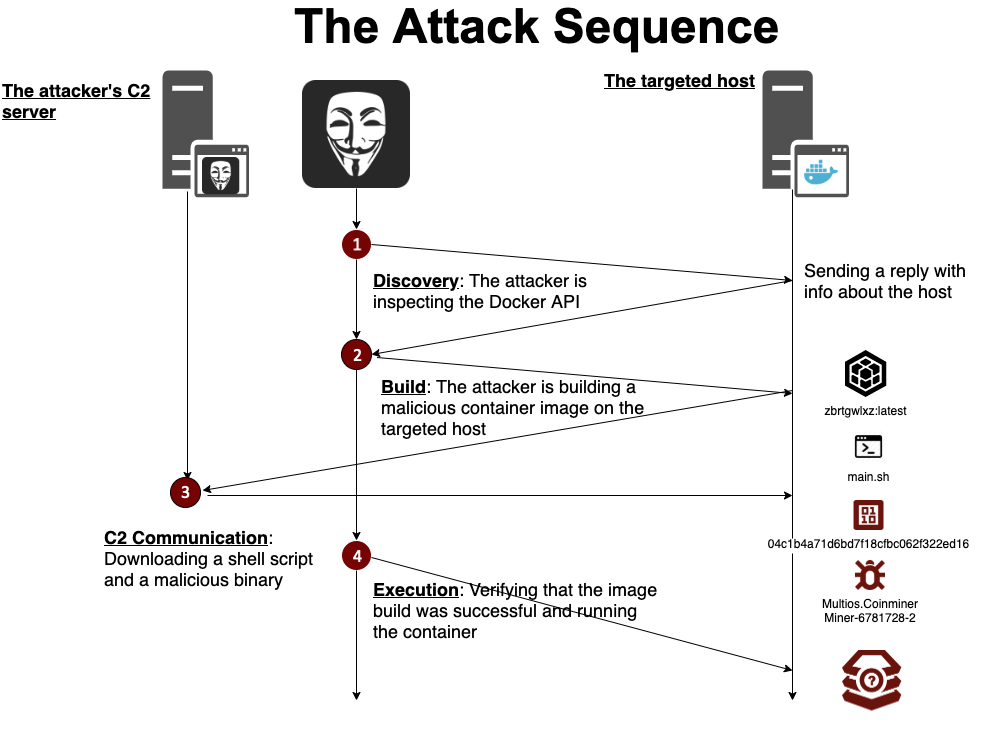
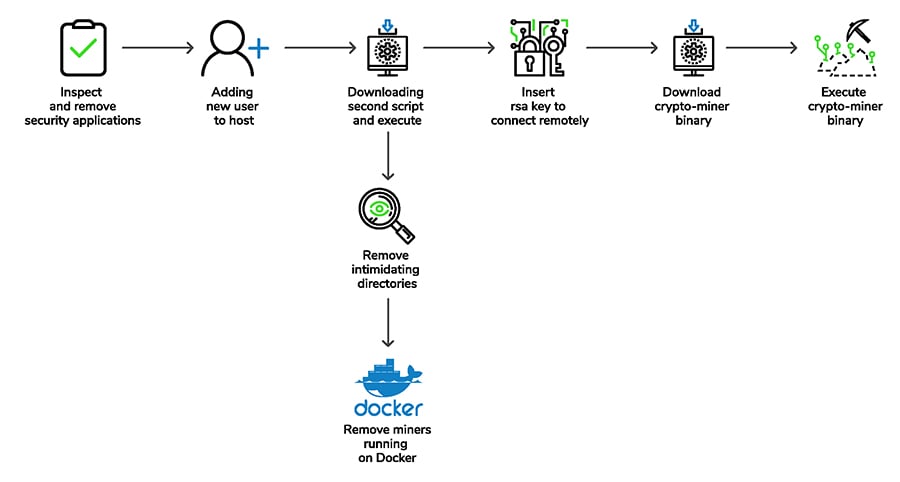
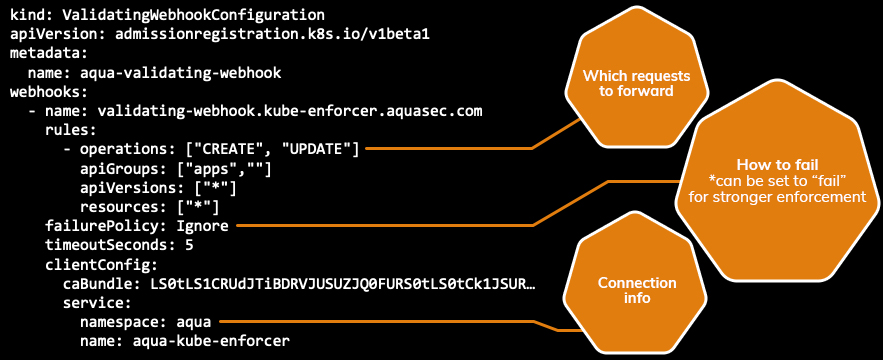
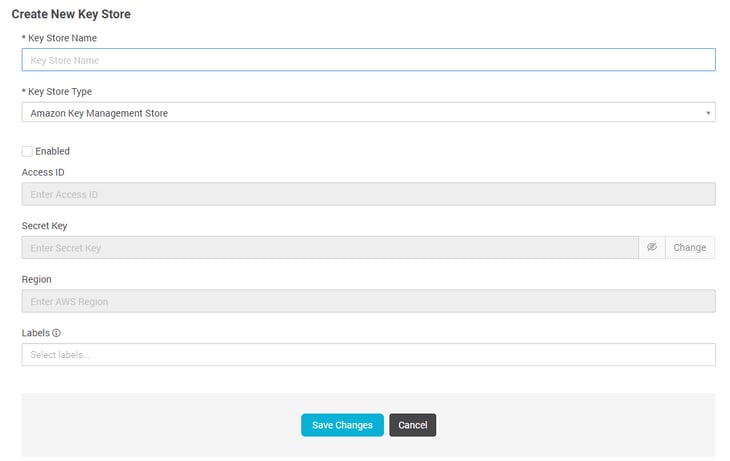
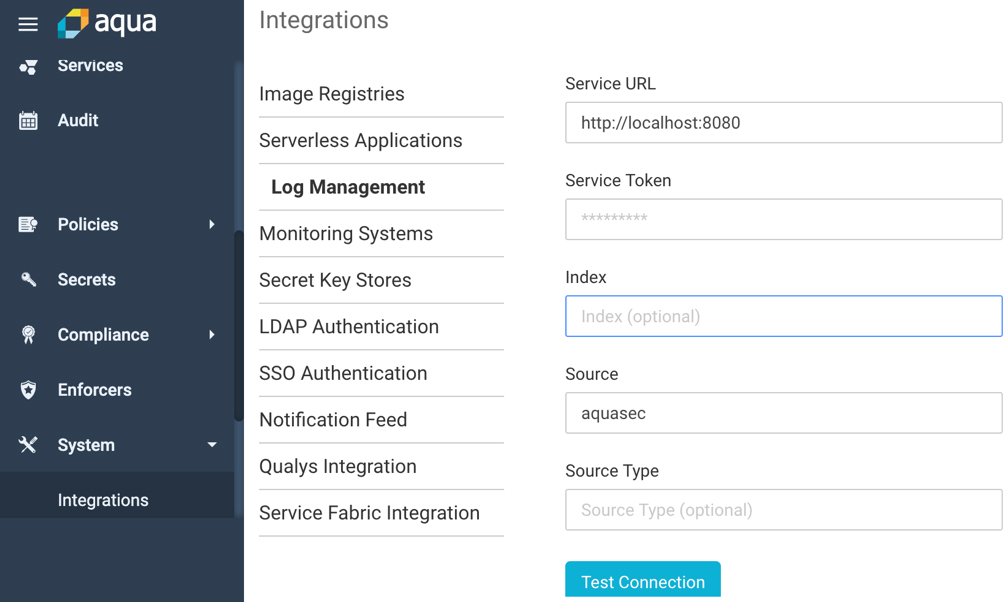
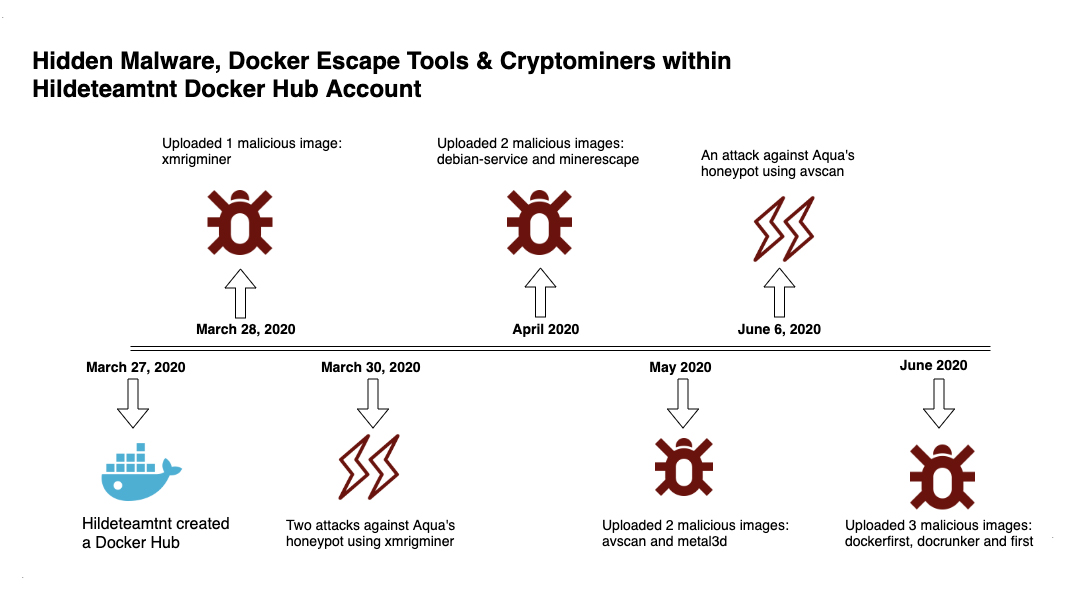
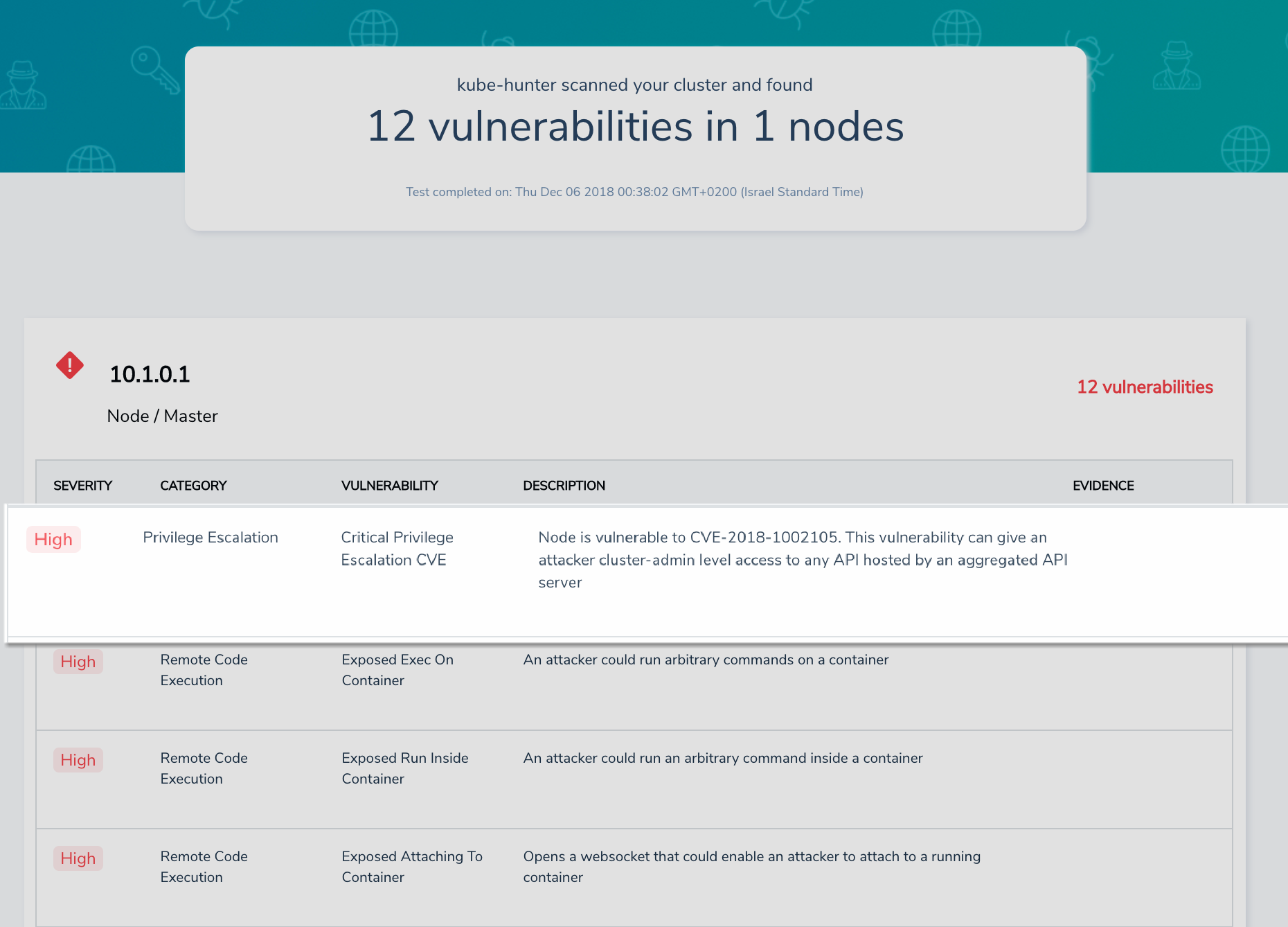
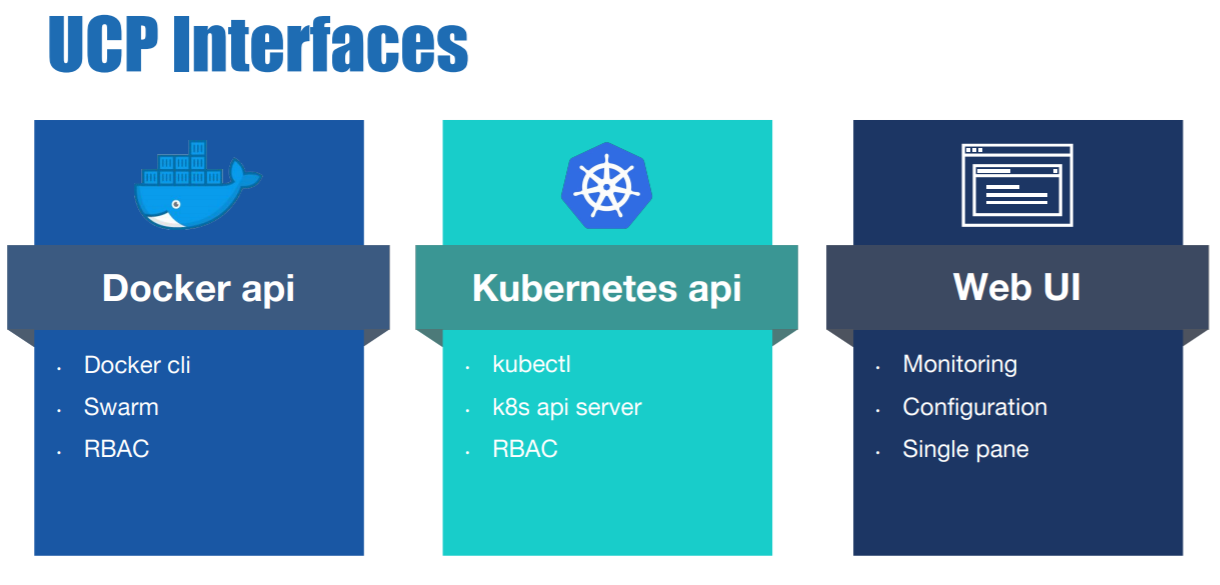
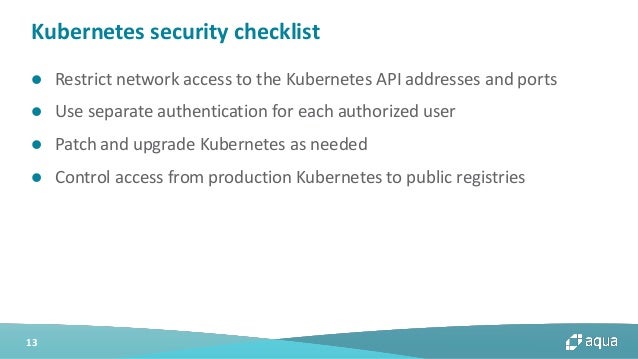
Aqua container security api. Aqua s container security platform provides full visibility into container activity allowing organizations to detect and prevent suspicious activity and attacks providing transparent automated security while helping to enforce policy and simplify regulatory compliance. Aqua continuously monitors azure container registry acr to ensure that no new vulnerabilities are present in stored images. Aqua security research report shows increase in organized attacks on cloud native infrastructure and software supply chain. Aqua s container security platform provides full visibility into container activity allowing organizations to detect and prevent.
In theory developers are assuming more responsibility for implementing cybersecurity controls within the context of a devsecops process. Aqua security is the largest pure play cloud native security company providing customers the freedom to innovate and run their businesses with minimal friction. Aqua security enables enterprises to secure their container based and cloud native applications from development to production accelerating container adoption and bridging the gap between devops and it security. Aqua s container security platform provides full visibility into container activity allowing organizations to detect and prevent.
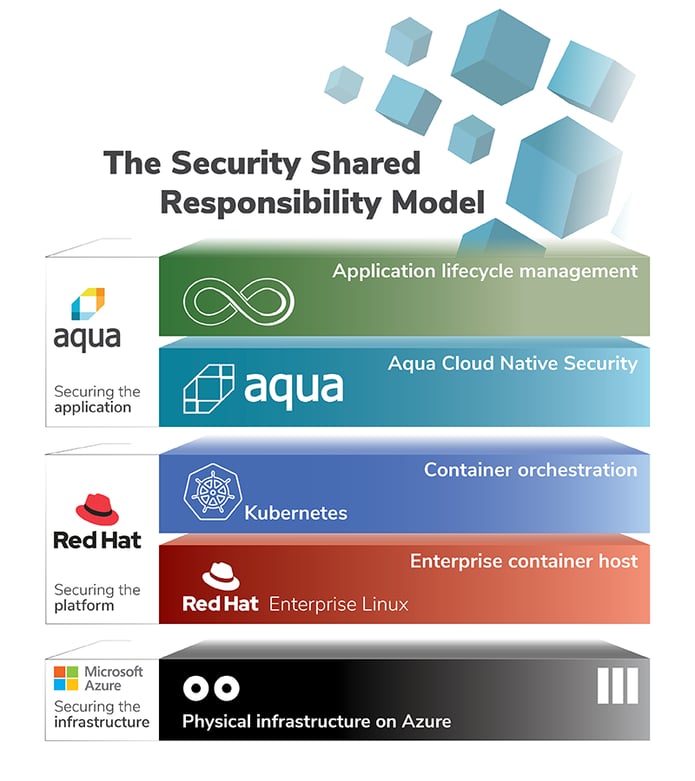
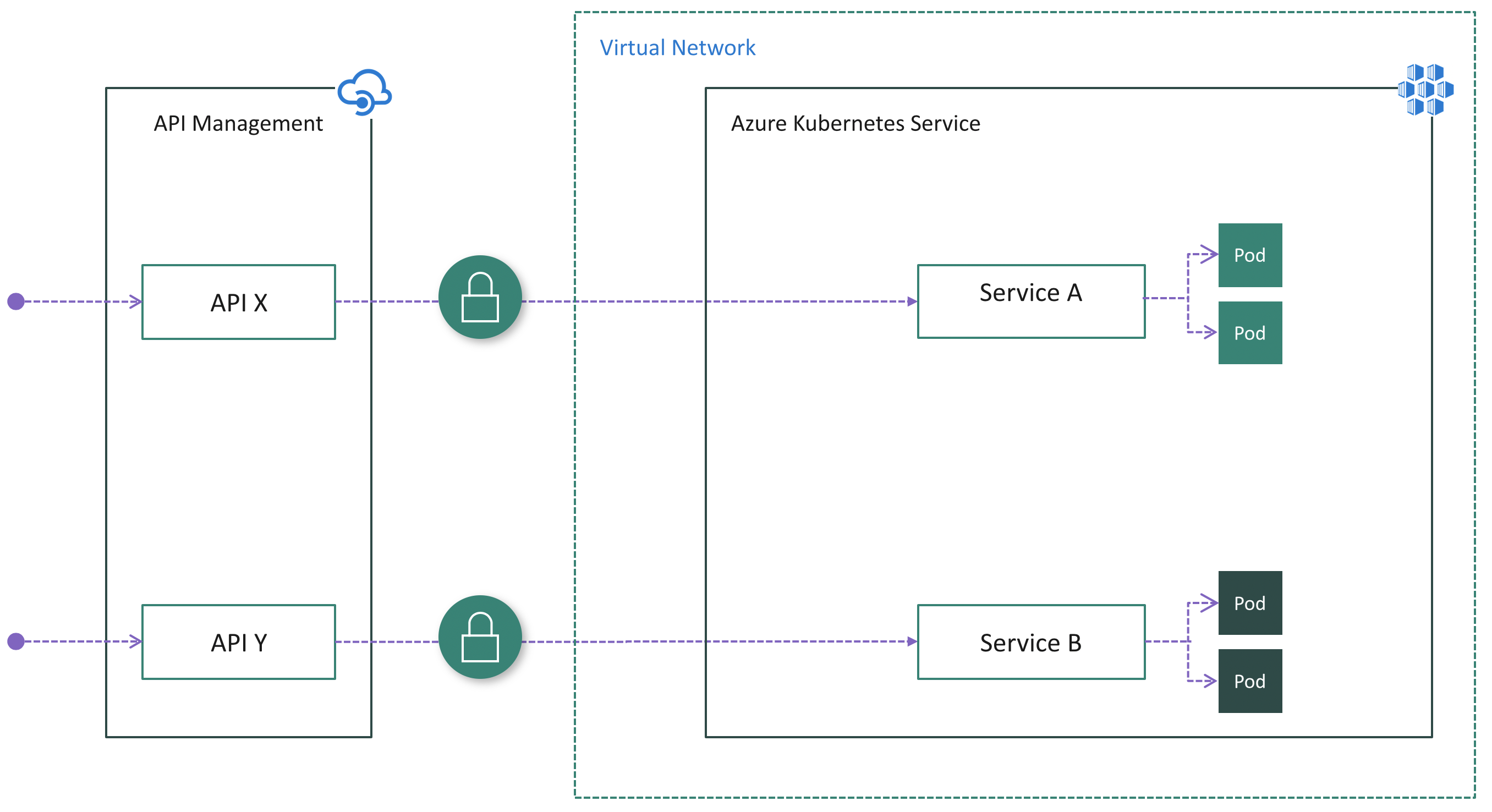
Aqua security enables enterprises to secure their container based and cloud native applications from development to production accelerating container adoption and bridging the gap between devops and it security. The complete cloud native security platform unleash the full potential of your cloud native transformation and accelerate innovation with the confidence that your cloud native applications are secured from start to finish at any scale. Aqua platform protects your entire stack on any cloud across vms containers and serverless. The aqua cloud native security platform provides prevention detection and response automation across the entire application lifecycle to secure the build secure cloud infrastructure and secure running workloads wherever they are deployed.
Aqua security is the largest pure play cloud native security company providing customers the freedom to innovate and run their businesses with minimal friction. The warning from aqua security regarding api ports comes at a time when responsibility for cybersecurity is in a state of flux within many it organizations. Aqua security enables enterprises to secure their container based and cloud native applications from development to production accelerating container adoption and bridging the gap between devops and it security. Automated security into your ci cd pipeline including aqua native plug in for azure devops formerly visual studio team services to prevent the introduction of vulnerabilities bad configurations or secrets into container images.